
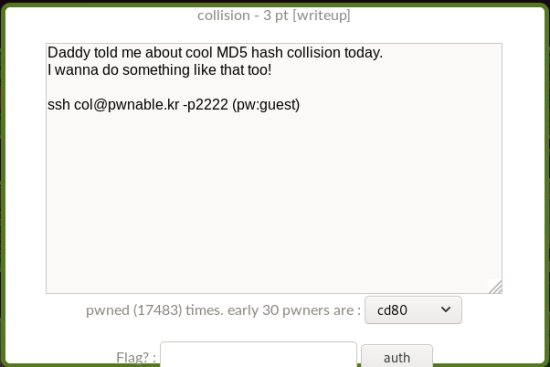
Wow… I had a feeling, but the difficulty’s on another level.
Thats absolutely lunatic, ōxō;;That’s absolutely lunatic, ōxō;;
ε-(´・`)
Perhaps because it involves a system hack,
it’s a whole level above the usual web-based
war games on Wargame.kr in terms of difficulty.
I ended up referring to someone else’s
solution while working through it.
And since posting the actual
source code would make the thread messy,
I’ll place it in a text file so it can simply be copy-pasted.
Anyway, let’s get started right away.

Right, if I’m having a punt at roughly translating
the gist of this in my own way,
it’s something like this:
So, you’re on about MD5 hash collisions then,
are we? (···) Right,anyway.
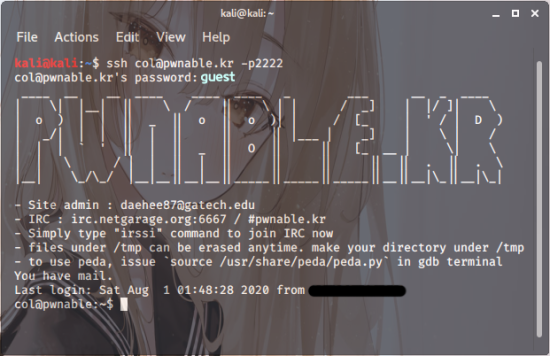
Right then, first things first,
open up yer Linux terminal.
Then you just wanna connect using
1 | ssh col@pwnable.kr -p2222 |
Now,the password right?
It won’t actually show up as you’re typing it
– don’t mind that,just bash it in,hit Enter,
and bam, you’re logged in. Easy peasy!

Right then next up,you just wanna whack in
the ls command to see what files you’ve got lurking around.
Now col you’d probably reckon that’s
some sort of executable or maybe even a Python file, right?
But the actual one we really need to be bothered with,
the crucial bit, is col.c
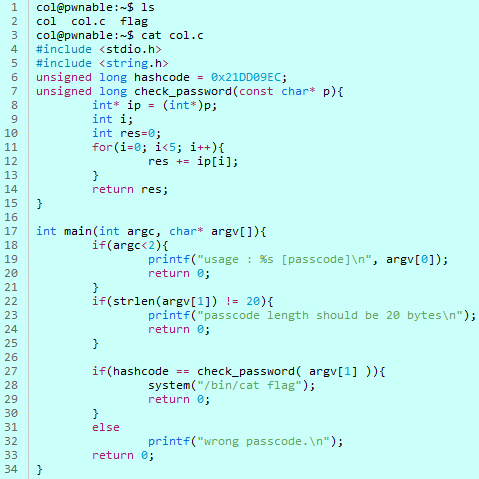
so if you have a proper gander at the main bit,
the password, right, that needs to be 20
characters long. And here’s the crucial part:
the hash code (0x21DD09EC) and
the password return value,
they’ve both gotta be
absolutely spot on, exactly the same.
No messing about with that, understood
That bash check_password(const char* p)
Bit, Yeah?
What it’s doing is, it’s taking chunks of the data
like, 4 bytes at a time – that’s the size of an int, innit?
– and it’s then accumulating those into ‘res’ five times.
So, the thinking is,
if you just add the exact same value five times over you should,
I reckon, get that hash code it’s after. Simple as that, really.
Derivation of results
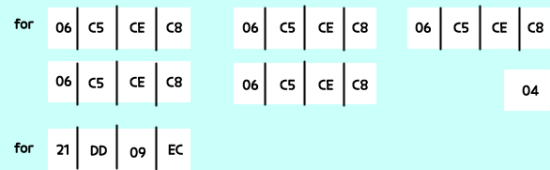
Right, so that’res’value,yeah?
That’s just the result of piling up
whatever came out of the ‘for’loop,
five times over.
And if you then,like,divvy that’res’value by five,
it turns out that the data
so if you then like,multiply this lot by five again
you’ll find you’re short by 0x4.So,
the assumption we’re making here is
that the data is essentially four lots of0x6C5CEC8 and then one bit of 0x6C5CECC added in.

then,since it’s all about little endian,yeah?
All you need to do is just feed the program that data
in hexadecimal,in the exact sequence.
That’s the one.
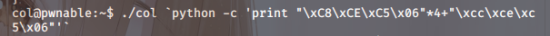
using Python for that, yeah?
Now, here’s the kicker, mind you:
when the program picks that up as an input
it’ll jolly well recognise it as a char.
So, you just gotta watch out for that. Proper careful,like.
Flag
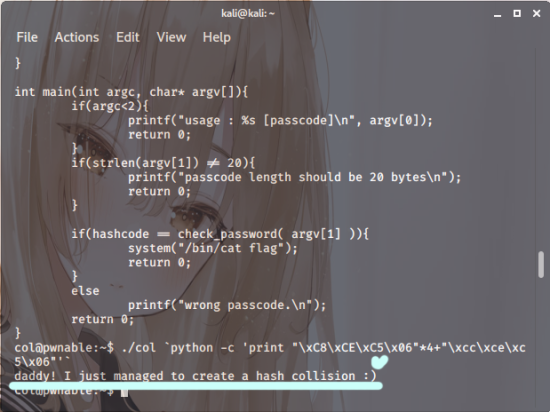
And with this rather handy key we’ve just nabbed
it’s back to the very beginning, isn’t it?
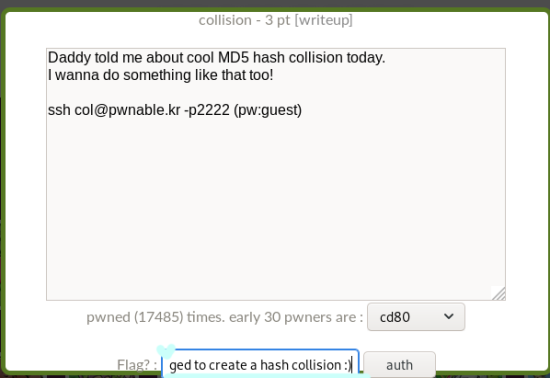
you just gotta punch in your key value.
And once that’s
sorted, hit the’auth’button Simples.
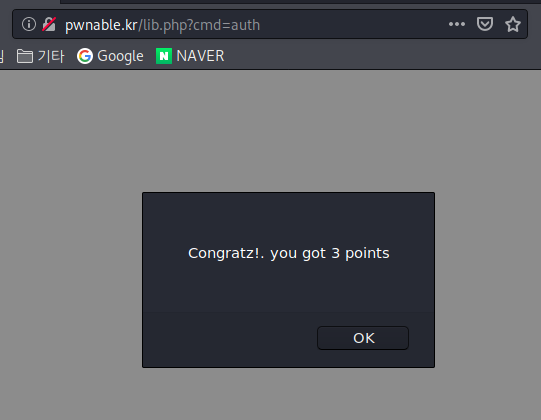
Right,and then you swing back round,
and there it is: marked up with a green dotted line.
Means you’ve bloody well sorted it, doesn’t it?
Right, well that’s the whole bloody spiel done.
Cheers for wading through all that, yeah : )

Alright then,
hope you have a decent day and
all your bits and bobs go swimmingly.
It’s a proper scorcher out there,
mind you, so try not to go getting heatstroke, yeah?
And, uh, watch out for that bloody Wuhan pneumonia. Stay safe, mate. : )
